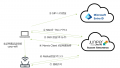
Juniper SRX シリーズが DS-Lite に対応したので家庭用として一般的な SRX300 を使用して接続しました。
Junos 23.2R1において、さらにFQDNでトンネル接続先アドレスを指定したり、トンネルソースアドレスを指定したインターフェイスから取得する機能をサポートしました(ドキュメント)。
Junos(SRX)でDS-Liteを使用してみる ver 2023 #juniper – Qiita
環境
回線:NTT 東日本フレッツ光、光電話なし(/64 RA環境)
プロバイダ:IIJmio光 IPoE オプション (インターネットマルチフィード提供 transix DS-Lite)
機器:SRX300 Junos: 23.2R2.21 (24.2R2-S2.5, 25.2R1でも確認済み)
ONU — (ge-0/0/0) SRX300 (irb.0) — PC(Windows, IPv4 のみ)
設定
(SRX300シリーズの場合) inet6 のモードが flow-based になっていないため、以下を設定し再起動が必要。
set security forwarding-options family inet6 mode flow-basedge-0/0/0 が RA(router advertisement) と DHCPv6 を受け取るように設定
delete interfaces ge-0/0/0 unit 0
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-type autoconfig
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-ia-type ia-na
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-identifier duid-type duid-ll
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client update-server
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client req-option dns-server
set protocols router-advertisement interface ge-0/0/0.0 passive-modeIPIP6 (IPv4 over IPv6) トンネルを作成し、 宛先を FQDN で指定(ここが Junos 23.2 で対応)
set interfaces ip-0/0/0 unit 0 tunnel encap-type ipv6
set interfaces ip-0/0/0 unit 0 tunnel source-interface ge-0/0/0.0
set interfaces ip-0/0/0 unit 0 tunnel destination-hostname gw.transix.jp
set interfaces ip-0/0/0 unit 0 family inetIPv4 の next-hop を上記のトンネルに指定
set routing-options static route 0.0.0.0/0 next-hop ip-0/0/0.0ip-0/0/0.0 インターフェースを security zone untrust に割り当て
set security zones security-zone untrust interfaces ip-0/0/0.0WAN 側の security zone にフレッツからの DHVPv6 の受信を許可
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services dhcpv6各種確認・トラブルシュート
IPv6 アドレスの取得確認
root> show interfaces ge-0/0/0
Physical interface: ge-0/0/0, Enabled, Physical link is Up
Interface index: 139, SNMP ifIndex: 515
Link-level type: Ethernet, MTU: 1514, LAN-PHY mode, Link-mode: Full-duplex,
Speed: 1000mbps, BPDU Error: None, Loop Detect PDU Error: None,
Ethernet-Switching Error: None, MAC-REWRITE Error: None, Loopback: Disabled,
Source filtering: Disabled, Flow control: Disabled, Auto-negotiation: Enabled,
Remote fault: Online
Device flags : Present Running
Interface Specific flags: Internal: 0x0
Interface flags: SNMP-Traps Internal: 0x0
Link flags : None
CoS queues : 8 supported, 8 maximum usable queues
Current address: 4c:6d:58:01:12:23, Hardware address: 4c:6d:58:01:12:23
Last flapped : 2025-08-12 07:21:03 UTC (00:06:10 ago)
Input rate : 960 bps (0 pps)
Output rate : 520 bps (0 pps)
Active alarms : None
Active defects : None
PCS statistics Seconds
Bit errors 0
Errored blocks 0
Interface transmit statistics: Disabled
Logical interface ge-0/0/0.0 (Index 75) (SNMP ifIndex 523)
Flags: Up SNMP-Traps 0x0 Encapsulation: ENET2
Input packets : 215
Output packets: 24
Security: Zone: untrust
Allowed host-inbound traffic : dhcp tftp https
Protocol inet, MTU: 1500
Max nh cache: 100000, New hold nh limit: 100000, Curr nh cnt: 0,
Curr new hold cnt: 0, NH drop cnt: 0
Flags: Sendbcast-pkt-to-re
Protocol inet6, MTU: 1500
Max nh cache: 100000, New hold nh limit: 100000, Curr nh cnt: 1,
Curr new hold cnt: 0, NH drop cnt: 0
Flags: None
Addresses, Flags: Is-Default Is-Primary
Local: 2409:10:b1c0:1234:1234:abcd:feed:1234
Addresses, Flags: Is-Preferred 0x0
Destination: fe80::/64, Local: fe80::4e6d:1234:1234:1234IPv6 疎通確認
root> ping 2606:4700:4700::1111
PING6(56=40+8+8 bytes) 2409:10:b1c0:1234:1234:abcd:feed:1234 --> 2606:4700:4700::1111
16 bytes from 2606:4700:4700::1111, icmp_seq=1 hlim=57 time=7.035 ms
16 bytes from 2606:4700:4700::1111, icmp_seq=2 hlim=57 time=6.601 ms
16 bytes from 2606:4700:4700::1111, icmp_seq=3 hlim=57 time=7.945 ms
^C
--- 2606:4700:4700::1111 ping6 statistics ---
4 packets transmitted, 3 packets received, 25% packet loss
round-trip min/avg/max/std-dev = 6.601/7.194/7.945/0.560 msip-0/0/0.0 が作られ、up になっていること
root> show interfaces terse
Interface Admin Link Proto Local Remote
ge-0/0/0 up up
ge-0/0/0.0 up up inet6 2409:10:b1c0:1234:1234:abcd:feed:1234
fe80::4e6d:1234:1234:1234/64
gr-0/0/0 up up
ip-0/0/0 up up
ip-0/0/0.0 up up inet
lsq-0/0/0 up up
lt-0/0/0 up up
mt-0/0/0 up up
sp-0/0/0 up up
(snip)経路の確認。inet.0 のデフォルトルートがトンネル宛になっていること。
root> show route
inet.0: 3 destinations, 3 routes (3 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Static/5] 00:00:11
> via ip-0/0/0.0
10.10.10.10/32 *[Direct/0] 00:04:15
> via lo0.0
192.168.1.1/32 *[Local/0] 00:04:15
RejectIPv4 でのインターネット疎通確認
(IPv4 を持つインターフェースが up になっていない場合 ping: sendto: Can’t assign requested address が発生する。何かつないで irb を up にするか、lo0.0 を作成する)
root> ping 1.1.1.1
PING 1.1.1.1 (1.1.1.1): 56 data bytes
64 bytes from 1.1.1.1: icmp_seq=0 ttl=59 time=9.185 ms
64 bytes from 1.1.1.1: icmp_seq=1 ttl=59 time=6.724 ms
64 bytes from 1.1.1.1: icmp_seq=2 ttl=59 time=6.842 ms
^C
--- 1.1.1.1 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 6.724/7.584/9.185/1.133 msAFTR のアドレスが解決できているか確認
root> ping gw.transix.jp
PING6(56=40+8+8 bytes) 2409:10:b1c0:1234:1234:abcd:feed:1234 --> 2404:8e00::feed:102
16 bytes from 2404:8e00::feed:102, icmp_seq=0 hlim=59 time=6.808 ms
^C
--- gw.transix.jp ping6 statistics ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max/std-dev = 6.808/6.808/6.808/0.000 msトンネル宛に通信がされているかカウンタを確認(青線部分は gw.transix.jp の AFTR のv6アドレス)
root> show interfaces ip-0/0/0
Physical interface: ip-0/0/0, Enabled, Physical link is Up
Interface index: 149, SNMP ifIndex: 524
Type: IPIP, Link-level type: IP-over-IP, MTU: Unlimited, Speed: 800mbps
Link flags : Keepalives DTE
Device flags : Present Running
Input rate : 264 bps (0 pps)
Output rate : 0 bps (0 pps)
Logical interface ip-0/0/0.0 (Index 86) (SNMP ifIndex 539)
Flags: Up Point-To-Point SNMP-Traps 0x0
IP-Header 2409:10:b1c0:1234:1234:abcd:feed:1234-2404:8e00::feed:102-41-64-0-0-00000000
Encapsulation: IPIP-NULL
Input packets : 163
Output packets: 214
Security: Zone: untrust
Protocol inet, MTU: 1460
Max nh cache: 0, New hold nh limit: 0, Curr nh cnt: 0, Curr new hold cnt: 0,
NH drop cnt: 0
Flags: Sendbcast-pkt-to-re参考資料
Junos(SRX)でDS-Liteを使用してみる ver 2023 #juniper – Qiita
その他
デフォルトコンフィグの DHCP サーバーを使う場合、name-server の設定が ge-0/0/0 の受信したものを引き継ぐようになっているが、DS-Lite の場合引継ぎ元がないため、明示的に設定が必要。
set access address-assignment pool junosDHCPPool family inet dhcp-attributes name-server 1.1.1.1tcp-mss を適宜調整
set security flow tcp-mss all-tcp mss 1420Full Config
set version 24.2R2-S2.5
set system host-name SRX300-dslite
set system root-authentication encrypted-password "XXXXXXXXXXXXXXXXXXXXXXXXX"
set system services netconf ssh
set system services ssh
set system services dhcp-local-server group jdhcp-group interface irb.0
set system services web-management https system-generated-certificate
set system name-server 8.8.8.8
set system name-server 8.8.4.4
set system syslog archive size 100k
set system syslog archive files 3
set system syslog user * any emergency
set system syslog file interactive-commands interactive-commands any
set system syslog file messages any notice
set system syslog file messages authorization info
set system max-configurations-on-flash 5
set system max-configuration-rollbacks 5
set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval
set system phone-home server https://redirect.juniper.net
set system phone-home rfc-compliant
set security pki ca-profile ISRG_Root_X1 ca-identity ISRG_Root_X1
set security pki ca-profile ISRG_Root_X1 pre-load
set security pki ca-profile Lets_Encrypt ca-identity Lets_Encrypt
set security pki ca-profile Lets_Encrypt enrollment url https://acme-v02.api.letsencrypt.org/directory
set security forwarding-options family inet6 mode flow-based
set security flow tcp-mss all-tcp mss 1420
set security screen ids-option untrust-screen icmp ping-death
set security screen ids-option untrust-screen ip source-route-option
set security screen ids-option untrust-screen ip tear-drop
set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200
set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048
set security screen ids-option untrust-screen tcp syn-flood timeout 20
set security screen ids-option untrust-screen tcp land
set security nat source rule-set trust-to-untrust from zone trust
set security nat source rule-set trust-to-untrust to zone untrust
set security flow tcp-mss all-tcp mss 1420
set security nat source rule-set trust-to-untrust rule source-nat-rule match source-address 0.0.0.0/0
set security nat source rule-set trust-to-untrust rule source-nat-rule then source-nat interface
set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any
set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any
set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any
set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit
set security policies from-zone trust to-zone trust policy trust-to-trust match source-address any
set security policies from-zone trust to-zone trust policy trust-to-trust match destination-address any
set security policies from-zone trust to-zone trust policy trust-to-trust match application any
set security policies from-zone trust to-zone trust policy trust-to-trust then permit
set security policies pre-id-default-policy then log session-close
set security zones security-zone trust host-inbound-traffic system-services all
set security zones security-zone trust host-inbound-traffic protocols all
set security zones security-zone trust interfaces irb.0
set security zones security-zone untrust screen untrust-screen
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services dhcp
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services tftp
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services https
set security zones security-zone untrust interfaces ge-0/0/0.0 host-inbound-traffic system-services dhcpv6
set security zones security-zone untrust interfaces ge-0/0/7.0 host-inbound-traffic system-services dhcp
set security zones security-zone untrust interfaces ge-0/0/7.0 host-inbound-traffic system-services tftp
set security zones security-zone untrust interfaces dl0.0 host-inbound-traffic system-services tftp
set security zones security-zone untrust interfaces ip-0/0/0.0
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-type autoconfig
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-ia-type ia-na
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client client-identifier duid-type duid-ll
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client req-option dns-server
set interfaces ge-0/0/0 unit 0 family inet6 dhcpv6-client update-server
set interfaces ip-0/0/0 unit 0 tunnel encap-type ipv6
set interfaces ip-0/0/0 unit 0 tunnel source-interface ge-0/0/0.0
set interfaces ip-0/0/0 unit 0 tunnel destination-hostname gw.transix.jp
set interfaces ip-0/0/0 unit 0 family inet
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/4 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/5 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/6 unit 0 family ethernet-switching vlan members vlan-trust
set interfaces ge-0/0/7 unit 0 family inet dhcp vendor-id Juniper-srx320
set interfaces cl-1/0/0 dialer-options pool 1 priority 100
set interfaces dl0 unit 0 family inet negotiate-address
set interfaces dl0 unit 0 family inet6 negotiate-address
set interfaces dl0 unit 0 dialer-options pool 1
set interfaces dl0 unit 0 dialer-options dial-string 1234
set interfaces dl0 unit 0 dialer-options always-on
set interfaces irb unit 0 family inet address 192.168.1.1/24
set interfaces lo0 unit 0 family inet address 10.10.10.10/32
set access address-assignment pool junosDHCPPool family inet network 192.168.1.0/24
set access address-assignment pool junosDHCPPool family inet range junosRange low 192.168.1.2
set access address-assignment pool junosDHCPPool family inet range junosRange high 192.168.1.254
set access address-assignment pool junosDHCPPool family inet dhcp-attributes name-server 1.1.1.1
set access address-assignment pool junosDHCPPool family inet dhcp-attributes router 192.168.1.1
set access address-assignment pool junosDHCPPool family inet dhcp-attributes propagate-settings ge-0/0/0.0
set vlans vlan-trust vlan-id 3
set vlans vlan-trust l3-interface irb.0
set protocols router-advertisement interface ge-0/0/0.0 passive-mode
set protocols l2-learning global-mode switching
set protocols rstp interface all
set routing-options static route 0.0.0.0/0 next-hop ip-0/0/0.0※ NAT は AFTR 側で行われるので不要ですが、デフォルトコンフィグに追記で設定しているので入れたままにしてます。


コメント